kSMBd: a quick overview
Table of Contents
Introduction
Nowadays, it is usual for a company to expose a file sharing service. Whether exposed on the Internet or on a LAN, these services are among the most commonly deployed.
Given the criticality of such services and the attack surface they expose, the security researchers’ interest to break through it is quite important. For instance, the Pwn2Own competition offers a good number of NAS system entries each year.
In order to serve files, several protocols have been elaborated:
- NFS (Network File System)
- SMB (Server Message Block)
- AFP (Apple File Protocol)
- 9P (Plan 9 Filesystem Protocol)
- etc.
Their usage may vary depending on the ecosystem around the file sharing service and/or its exposition.
For each of these protocols, multiple implementations exist:
| Protocol | Implementations |
|---|---|
| NFS | Windows, Linux |
| SMB | Windows, samba, Linux (wink wink) |
| AFP | Netatalk |
| 9P | Qemu, WSL |
In this blogpost, we introduce the analysis of one SMB implementation: kSMBd. It will be followed up by a talk @ OffensiveCon 2023 named Abusing Linux in-kernel SMB server to gain kernel remote code execution.
kSMBd
At the end of 2021, an LWN article caught our attention. A new SMB server implementation was being actively developed and on top of that, it was an in-kernel Linux implementation. Thus, our spring break was booked.
Presentation
kSMBd is a Linux kernel module that implements the SMB/CIFS protocol. It is developed by Namjae Jeon and is open source. This module has eventually been pulled upstream in the Linux kernel. As a consequence, it is shipped by distributions, such as Ubuntu or OpenWrt. The main objective behind this new implementation and the reason why it resides in the kernel appears to be performance, by keeping most of the treatments inside the kernel, saving your precious CPU cycles.
Most of the publications related to kSMBd can be found on the SambaXP conference website. These talks were good starting points to understand where the project was going and what features we could expect.
kSMBd supports a lot of features that make it a very attractive project, such as:
- multiple dialects: SMB2.1 / SMB3.0 / SMB3.1.1
- oplock cache mechanism
- compound request
- SMB Direct (RDMA)
- ACL
- DCE/RPC
This kernel module supports Linux kernel 5.4 or later, and was incorporated into the mainline kernel with the 5.15 release.
Architecture overview
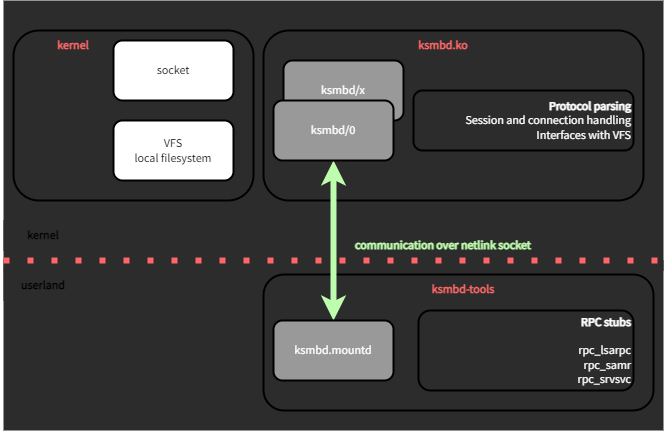
From a high-level perspective, the kSMBd architecture is split between user-land and kernel-land. Indeed, even if the aim of kSMBd is to increase performance by handling most of the file sharing service in the kernel, some components still reside in user-land.
The user-land component (ksmbd-tools) implements DCE/RPC endpoints such as:
rpc_lsarpc: Local Security Authority (Domain Policy) Remote Protocolrpc_samr: Security Account Manager (SAM) Remote Protocolrpc_srvsvc: Server Service Remote Protocol- etc.
On the other hand, the kernel-land module is focused on the protocol handling and the VFS compatibility.
Between user-land and kernel-land components, netlink is used as IPC and their interaction can be shown as below:
Attack surfaces
From our perspective, we identified three major attack surfaces in the kSMBd project to look at. This is clearly not an exhaustive list.
The first and most straightforward attack surface is the SMB protocol handler. This portion of code handles incoming SMB messages from the network and will maintain the induced state machine. This is the core of the server and regardless of the attack surface that is addressed, it is important to understand roughly how it works.
Another attack surface that is readily apparent is the virtual file system (VFS). The VFS implements the interaction with the host file system and might expose features such as ACL, streams and so on. In many cases, it provides a compatibility layer for the remote client.
Last but not least, the SMB protocol is a complex beast which not only allows remote users to tinker with files and folders but also to call Remote Procedure Call routines. Those RPC interfaces allow clients to request information about the remote system, such as listing the users or shares present on the SMB server. This is also a compatibility feature coming from the Windows world. From the three nominated attack surfaces, this is the only one implemented in user-space.
These three attack surfaces have been addressed during the analysis.
SMB core (kernel): compound request
From the first attack surface, we decided to analyze the SMB compound request handling.
Compound requests in the SMB protocol are a way for a client to group multiple SMB commands into a single SMB request. This can improve performance by reducing the number of network round-trips needed to complete a series of operations.
Each compound request contains a series of commands, which are processed sequentially by the server. The responses for each command are then combined into a single response message, which is sent back to the client.
Compound requests are used extensively in SMB, particularly for file and print operations, where multiple commands are often required to complete a given operation. By grouping these commands together, SMB is able to provide improved performance and reduced network overhead.
SMB feature (kernel): VFS
A VFS is an abstraction layer that sits between the file system and the client application, providing a unified view of the file system regardless of the underlying storage device.
In the context of SMB, a VFS is implemented on the server side and allows the server to present a consistent view of the file system to SMB clients, regardless of the underlying file system or storage technology being used. This is particularly useful in heterogeneous environments where different clients may be accessing the same file system using different protocols or operating systems.
The SMB VFS provides a number of features and benefits, including:
- Cross-platform support: The VFS allows SMB servers to provide a consistent view of the file system to clients running on different operating systems.
- Security: The VFS can enforce access control policies and other security measures to ensure that only authorized users have access to files and directories.
- Performance optimization: The VFS can perform caching and other optimizations to improve the performance of file system operations.
- Extensibility: The VFS can be extended to support additional file system features and functionality, such as encryption, compression, or versioning.
Overall, the SMB VFS is a key component of the protocol that enables servers to provide a flexible and robust file sharing solution to clients across a wide range of environments and use cases.
SMB feature (user): DCE/RPC
DCE/RPC stands for Distributed Computing Environment/Remote Procedure Call. In the SMB protocol, DCE/RPC is used as a means of communication between the client and server for performing various network operations.
In the context of SMB, DCE/RPC is used to enable a wide range of network operations, including file and printer sharing, authentication, and other administrative tasks. For example, when a client requests to access a file on a remote SMB server, the client sends an RPC request to the server using the DCE/RPC protocol. The server then processes the request and sends a response back to the client.
DCE/RPC is a critical component of the SMB protocol, as it enables efficient and secure communication between the client and server.
Generic SMB tooling
To avoid reinventing the wheel, we identified several tools and libraries that helped us during the analysis:
- smbtorture: Samba’s SMB test framework
- smbclient: Samba’s SMB/CIFS client
- impacket: a very good Python library to play with network protocols
- aioSMB: a pure-Python, fully asynchronous SMB library, inspired by impacket
- SMB_Fuzzer: an SMB fuzzer
Bugs identified
Our work session ended up with the discovery of 5 vulnerabilities affecting the kernel module and 5 others affecting the user-land daemon. All the vulnerabilities were reported through the Zero Day Initiave program.
| ZDI ID | ZDI CAN | CVE | Location | CVSS | Description |
|---|---|---|---|---|---|
| ZDI-22-1687 | ZDI-CAN-17815 | CVE-2022-47941 | Kernel | 5.3 | Linux Kernel ksmbd Memory Exhaustion Denial-of-Service Vulnerability |
| ZDI-22-1688 | ZDI-CAN-17771 | CVE-2022-47942 | Kernel | 8.5 | Linux Kernel ksmbd Heap-based Buffer Overflow Remote Code Execution Vulnerability |
| ZDI-22-1689 | ZDI-CAN-17818 | CVE-2022-47938 | Kernel | 6.5 | Linux Kernel ksmbd Out-Of-Bounds Read Denial-of-Service Vulnerability |
| ZDI-22-1690 | ZDI-CAN-17816 | CVE-2022-47939 | Kernel | 10.0 | Linux Kernel ksmbd Use-After-Free Remote Code Execution Vulnerability |
| ZDI-22-1691 | ZDI-CAN-17817 | CVE-2022-47943 | Kernel | 9.6 | Linux Kernel ksmbd Out-Of-Bounds Read Information Disclosure Vulnerability |
| ZDI-23-687 | ZDI-CAN-17770 | not yet defined | User | 9.8 | not yet defined |
| ZDI-23-688 | ZDI-CAN-17820 | not yet defined | User | 8.1 | not yet defined |
| ZDI-23-689 | ZDI-CAN-17821 | not yet defined | User | 7.5 | not yet defined |
| ZDI-23-690 | ZDI-CAN-17822 | not yet defined | User | 9.8 | not yet defined |
| ZDI-23-691 | ZDI-CAN-17823 | not yet defined | User | 7.5 | not yet defined |
Please note that the details regarding the user-land daemon vulnerabilities have not been published yet.
Disclosure timeline
- 2022-07-03: Vulnerabilities reported to ZDI
- 2022-07-29: CVE-2022-47941, CVE-2022-47938, CVE-2022-47939, CVE-2022-47943 are fixed in the kSMBd project
- 2022-08-01: CVE-2022-47941, CVE-2022-47938, CVE-2022-47939, CVE-2022-47943 are fixed in the kernel
- 2022-08-02: CVE-2022-47942 is fixed in the kSMBd project
- 2022-08-04: CVE-2022-47942 is fixed in the kernel
- 2022-08-17: Release of the Linux kernel version 5.15.61 (CVE-2022-47941 & CVE-2022-47938 & CVE-2022-47939)
- 2022-08-21: Release of the Linux kernel version 5.15.62 (CVE-2022-47943 & CVE-2022-47942)
- 2022-10-17: Fix in the kernel shipped by Ubuntu 22.04
- 2022-12-22/23: Coordinated public release of advisories for the kernel-land vulnerabilities (
Merry Christmas 🎅) - 2023-01-23: Advisory updated
- 2023-05-18: Coordinated public release of advisories for the user-land vulnerabilities
- 2023-05-19: Talk @ OffensiveCon
It goes without saying that the dates chosen for the public releases were out of our range of actions.
Conclusion
This article briefly presented the results of our analysis of kSMBd. The exploitation of some of the kernel vulnerabilities, resulting in a kernel RCE, will be presented at OffensiveCon 2023.