Artillery was a web challenge of the Cyber Apocalypse 2021 CTF organized by HackTheBox. We were given the source code of the server to help us solve the challenge. This challenge was a nice opportunity to learn more about XXE vulnerabilities.
One of the least solved challenges, yet probably not the most difficult one. It is a Hardware challenge, though it is significantly different from the other challenges of this category. The first thing to spot is that when starting the challenge machine, we have access to two network services:
- an HTTP server, requesting an authentication
- an AMQP broker,
rabbitmq
Off-the-grid was the 4th hardware challenge of the Cyber Apocalypse 2021 CTF organized by HackTheBox.
We were given an Saleae trace and schematics to analyse. Thalium was one of the very first of 99 players to complete it.
Wii-Phit was the only Hard crypto challenge designed by CryptoHack for the Cyber Apocalypse 2021 CTF (there were also 4 challenges categorized as Insane though).
There is already an excellent writeup by the challenge organizers:
one could recognize a well known equation related to the Erdős–Straus conjecture, some participants used Z3.
We took a different approach.
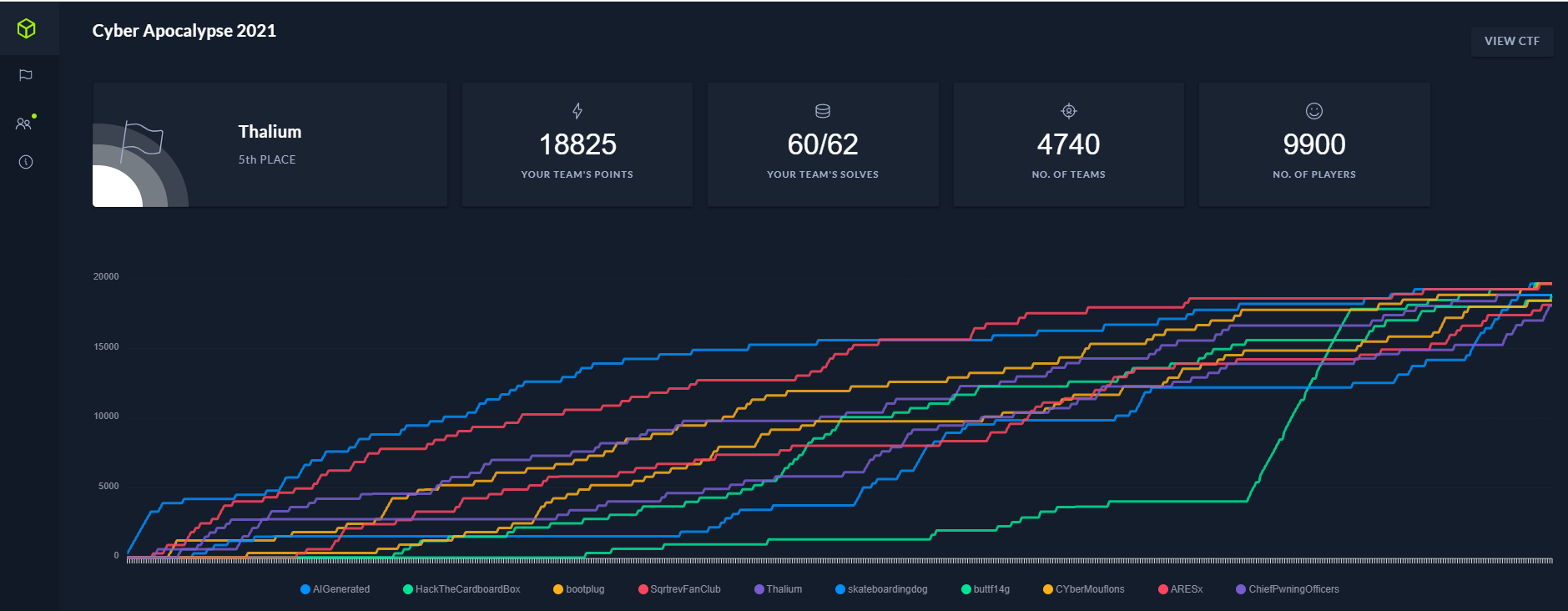
Thalium participated in the Cyber Apocalypse 2021 CTF organized last week by HackTheBox.
It was a great success with 4,740 teams composed of around 10,000 hackers from all over the world.
Our team finished in fifth place and solved sixty out of the sixty-two challenges:
This article explains how we solved each pwn challenge and what tools we used, it is written to be accessible to beginners:
Virtual Machine Introspection (VMI) is an extremely powerful technique to explore a guest OS.
Directly acting on the hypervisor allows a stealth and precise control of the guest state, which means its CPU context as well as its memory.
Basically, a common use case in VMI consists in (1) setting a breakpoint on an address, (2) wait for a break and (3) finally read some virtual memory.
For example, to simply monitor the user file writing activity on Windows, just set a breakpoint on the NtWriteFile function in kernel land.
Once triggered, you can retrieve the involved process and capture its corresponding callstack.
All these actions eventually require accessing the guest virtual memory.
Icebox is a VMI (Virtual Machine Introspection) framework enabling you to stealthily trace and debug any kernel or user code system-wide.
All Icebox source code can be found on our github page.
Try Icebox
Icebox now comes with full Python bindings enabling fast prototyping on top of VMI, whether you want to trace a user process or inspect the kernel internals.
The core itself is in C++ and exposes most of its public functions into an icebox Python 3 module.
